This site documents the technical contracts for interacting with the Document Service, an API provided by Inmar Intelligence. The Document Service is a centralized repository for storing and retrieving documents.
When onboarded by Inmar Intelligence to use the Document Service, each client will be provided with credentials to interact with the API:
A client ID and client secret pair for authorization token generation (see Authorization section below)
The below sequence diagram outlines the order of calls necessary to interact with the Document Service. Read the technical documentation via the link below to learn more about the individual endpoints.
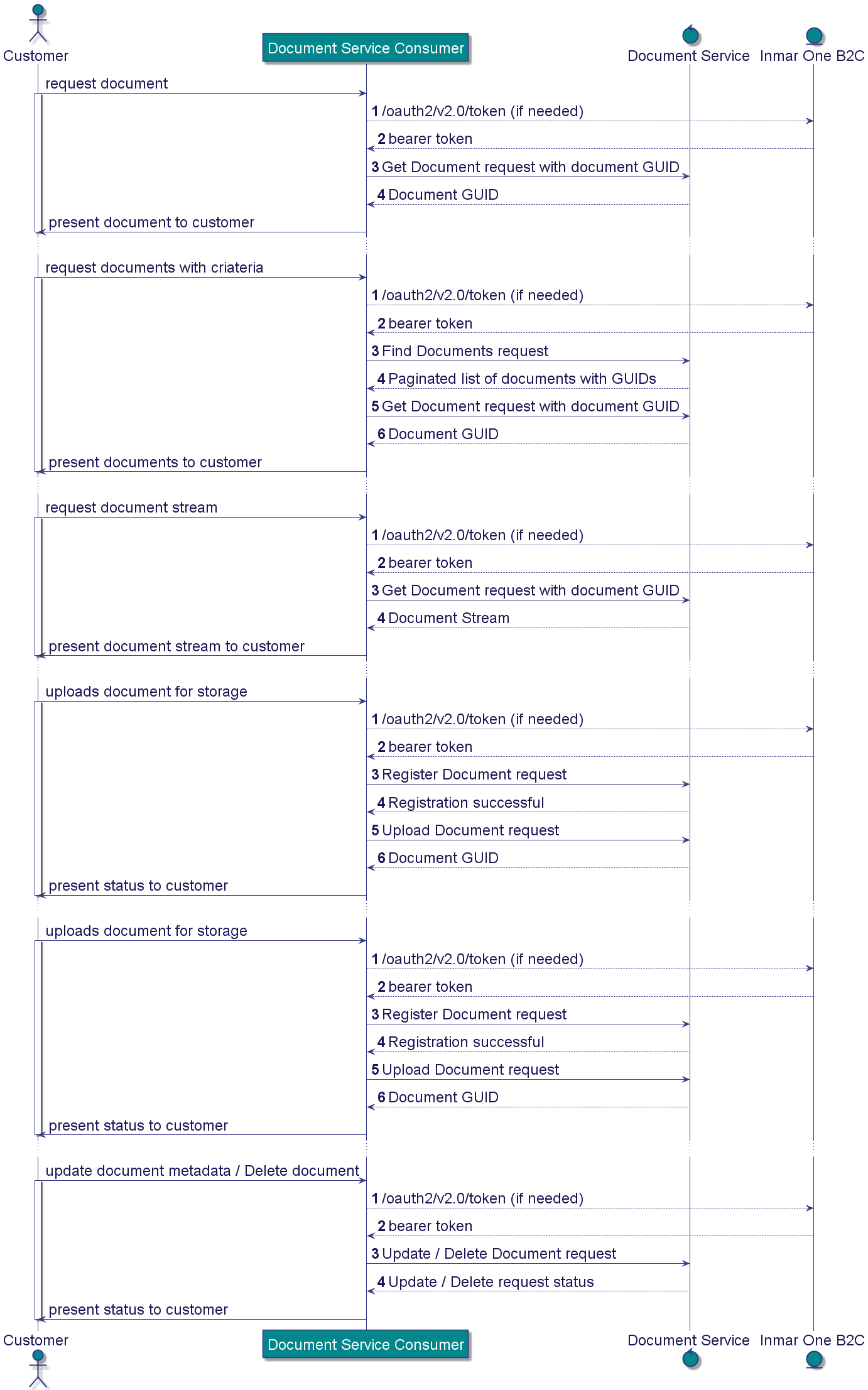
Authorization
The Document Service uses Azure Active Directory B2C for a token generation under the Inmar One SSO tenant. Inmar One SSO is Inmar's solution for customer single sign-on access to Inmar applications.
To generate a token, make a request to POST https://login.microsoftonline.com/utinmaronessoaadb2c.onmicrosoft.com/oauth2/v2.0/token with a body of content type multipart/form-data (see form data example here) containing the following fields:
client_id: client ID credential given to the client upon onboardingclient_secret: client secret credential given to the client upon onboardinggrant_type: should be set to "client_credentials"scope: should be set to "https://utinmaronessoaadb2c.onmicrosoft.com/1dc3092e-c955-48c9-9d7d-9e723f73c1d4/.default"
The below is a sample HTTP request fitting the above requirements:
POST /utinmaronessoaadb2c.onmicrosoft.com/oauth2/v2.0/token HTTP/1.1Host: login.microsoftonline.comContent-Type: multipart/form-data;boundary="boundary"--boundaryContent-Disposition: form-data; name="client_id"{client_id}--boundaryContent-Disposition: form-data; name="client_secret"{client_secret}--boundaryContent-Disposition: form-data; name="grant_type"client_credentials--boundaryContent-Disposition: form-data; name="scope"
https://utinmaronessoaadb2c.onmicrosoft.com/1dc3092e-c955-48c9-9d7d-9e723f73c1d4/.default--boundary--
In its response, Azure AD B2C will provide you with a body that contains the token as well as its expiry in seconds (see example below). For the duration of that token's lifetime, the token should be passed in any call to the Document Service in the Authorization header using the format Bearer {token}. The token can be reused as many times as required until its lifetime expires, at which point Azure AD B2C should be called again to generate a new token.
{"token_type": "Bearer","expires_in": 3599,"ext_expires_in": 3599,"access_token": "{token}"}